STACK-X Cloud 2021 concluded on 17 November 2021 with a central focus on the new (and hopefully improved) Government on Commercial Cloud, dubbed GCC 2.0.
In this post, I will share my key takeaways and initial thoughts of the new features coming for GCC 2.0. Before that, if you are wondering what GCC is, let me give you a quick introduction.
What is GCC?
The Government on Commercial Cloud (GCC) platform aims to help Singapore government agencies adopt cloud quicker and safer by providing add-ons built around commercial cloud platforms such as Amazon Web Services, Microsoft Azure and Google Cloud Platform.
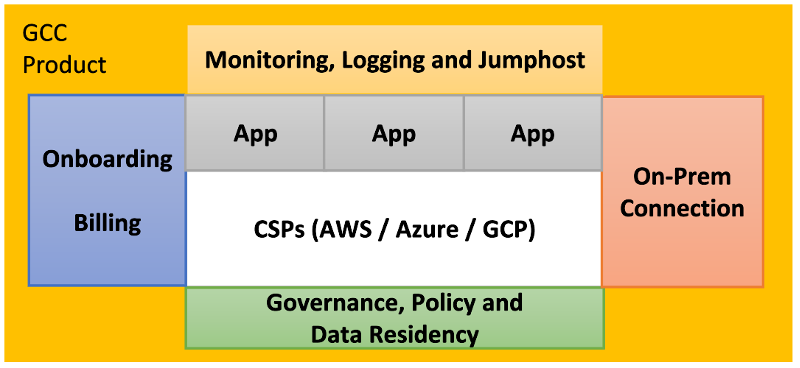
GCC is a “wrapper” platform that provides agencies with a consistent means to adopt commercial cloud offered by Amazon, Microsoft and Google.
from Singapore Government Developer Portal
In the following sections, I will highlight some of the issues in the current GCC platform and how GCC 2.0 aims to solve them.
TechPass: 1 Identity to Rule Them All
One of the most apparent issue in the current GCC platform is the multiple identities you need to maintain to use GCC. A typical user would need at least 3:
- VPN ID for establishing connection to GCC VPN.
- Cloud ID for cloud console access (for e.g. AWS console).
- Jump Host* ID for remote administrative access (for e.g. SSH. RDP) to cloud resources.
* also known to some as Bastian Host or Jump boxes
Maintaining multiple identities to access different parts of GCC is not only a hassle, but it can also increase GCC’s security risk due to the increased tendencies of users reusing the same password, as well as increasing the attack surface of having more than one identity store.
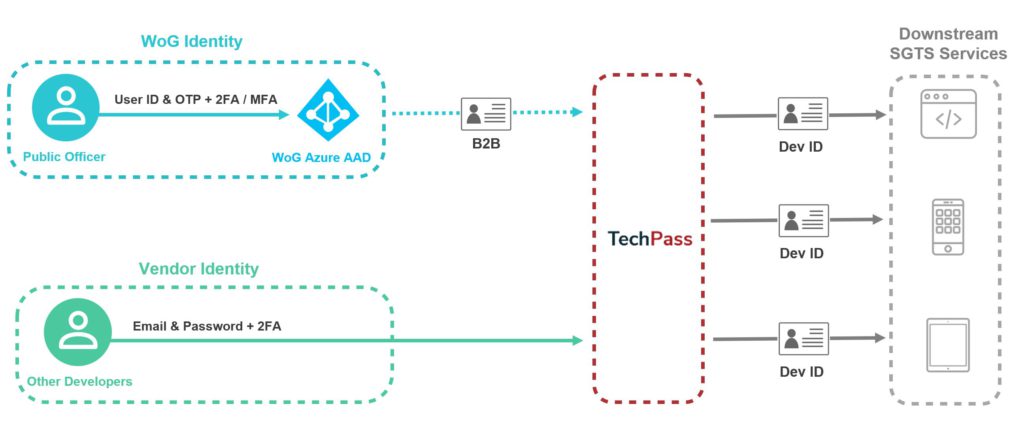
TechPass is an Identity & Access Management (IAM) and Single Sign On (SSO) Solution for services within the Singapore Government Technology Stack (SGTS). It is built to provide users with a seamless login experience across SG TechStack services and allow access control to be managed easily from a centralised location.
TechPass User Guide
TechPass is powered by Microsoft Azure Active Directory service. I believe that a single identity was always the envisioned goal for GCC, and the current set up was a stopgap measure due to technical or implementation difficulties.
MFA and Automation are not friends
My main worry for TechPass revolves around a general problem faced by Continuous Integration/Continuous Deployment (CI/CD) and DevOps automation when enforcing Single Sign-On (SSO) with multi-factor authentication (MFA) to produce short-lived credentials. For example, a Terraform CI/CD pipeline runner needs AWS credentials (usually in the form of Access and Secret Access Keys) to deploy to an AWS environment. If TechPass is enforced as the one and only means of authentication and authorization along with MFA, generating these credentials over and over again with MFA (manual step) feels like an anti-pattern for CI/CD.
SEED + DEEP: Trust Me
To access and use GCC services today, you must first establish a successful VPN connection to GCC VPN after passing some basic device check performed by the VPN client.
The Problem with VPN
COVID-19 lockdowns and restrictions meant that many employees were forced to work remotely. To access confidential data within the company’s private network, a VPN solution is the quickest way for many companies to allow employees to do so.
VPN offers binary networking access control. If you are connected to the VPN successfully, you often have networking access to all your corporate resources, regardless of your needs. If you are not connected to the VPN, you have no access.
Such binary access control goes against the principle of the least privilege, which states that each identity should only be allowed access to what they need – nothing more, nothing less. As the lines of a traditional network perimeter, like GCC, gets blurred with remote work proliferation, a safer solution is required.
Zero Trust with SEED
No product is complete without a good acronym. GCC 2.0 introduces the SEED platform as a key product for better security posture.
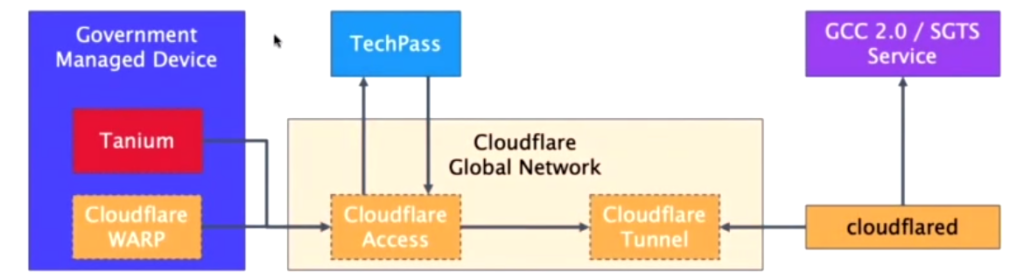
Security Suite for Engineering Endpoint Devices (SEED) is a Mobile Device Management (MDM) platform for the Government Commercial Cloud (GCC) 2.0 environment.
SEED Documentation
SEED is packaged with TechPass, Cloudflare Teams and DEEP, because apparently, we need more acronyms.
Development Environment Endpoint Posture (DEEP): The device management layer of MDM.
SEED Documentation
DEEP manages Microsoft Intune, Microsoft Defender Advanced Thread Protection (MDATP) and Tanium. The following diagram taken from one of the sessions in STACK-X Cloud 2021 gives a good overview of SEED.
MDM, Over-restriction & Bloat
Even though vendors can onboard their workstations to SEED in theory, the hard requirement to install a MDM software (Microsoft Intune) can potentially cause issues for workstations already managed by a MDM. Since macOS will also be required to install Microsoft Intune, it remains to be seen if there are undiscovered issues regarding compatibility and performance, especially with the new apple silicon, M1 macbooks.

During a Q&A session for the “Securing Access to GCC 2.0 from Engineering Devices” session in STACK-X 2021, the question was posted regarding split tunneling and Internet access on a SEED workstation. The answer was that Cloudflare WARP (the zero trust software) could be disabled for 3 hours, allowing for Internet browsing. However, during that time, the user will not be able to access GCC 2.0 services. This might be over-restrictive, hindering usage of SaaS products that needed to straddle between the SaaS backend servers and GCC 2.0.
Looking at the list of required software (Intune, Tanium, Cloudflare WARP, MDATP) to effectively secure your device, software bloat on a SEED workstation is big worry of mine. This may unintentionally prevent workstations with lower specs from onboarding to SEED for GCC 2.0.
Honourable Mentions
These are the rest of the new features that GCC 2.0 boasts. Since we do not have more publicly available information, I shall not go too deep in this post. Do expect future posts covering these once we have more information.
Most of these information came from the “What’s New in GCC 2.0” session during STACK-X Cloud 2021.
Cloud-Native First
Along with maturity of cloud-native products that provide the same services as GCC currently, GCC 2.0 will tap on cloud-native jump hosts (bastian hosts) and policy-as-code services.

For AWS, that would be the AWS Systems Manager Session Manager to provide SSH or Powershell access to Linux or Windows workloads respectively controlled with IAM. This is a great tool for managing Linux instances, but not suitable for graphical remote desktop access for Windows instances.
For policy-as-code enforcement, AWS Config was highlighted as an example to detect and potentially remediate security, tagging and other non-compliance constantly.
Giving Control (back) to Users
GCC 2.0 promises a “light touch” approach to tenant management. What caught my eye was the promise that certain networking functionalities such as VPC and Transit Gateway creation, VPC peering and IP addressing management will now be just an API call away.

This opens up a lot more opportunities for end-to-end automation by eliminating some of the manual processes revolving around the above-mentioned networking services. It will be interesting to see how this is implemented without compromising tenant boundaries.
Landing Zone with Terraform
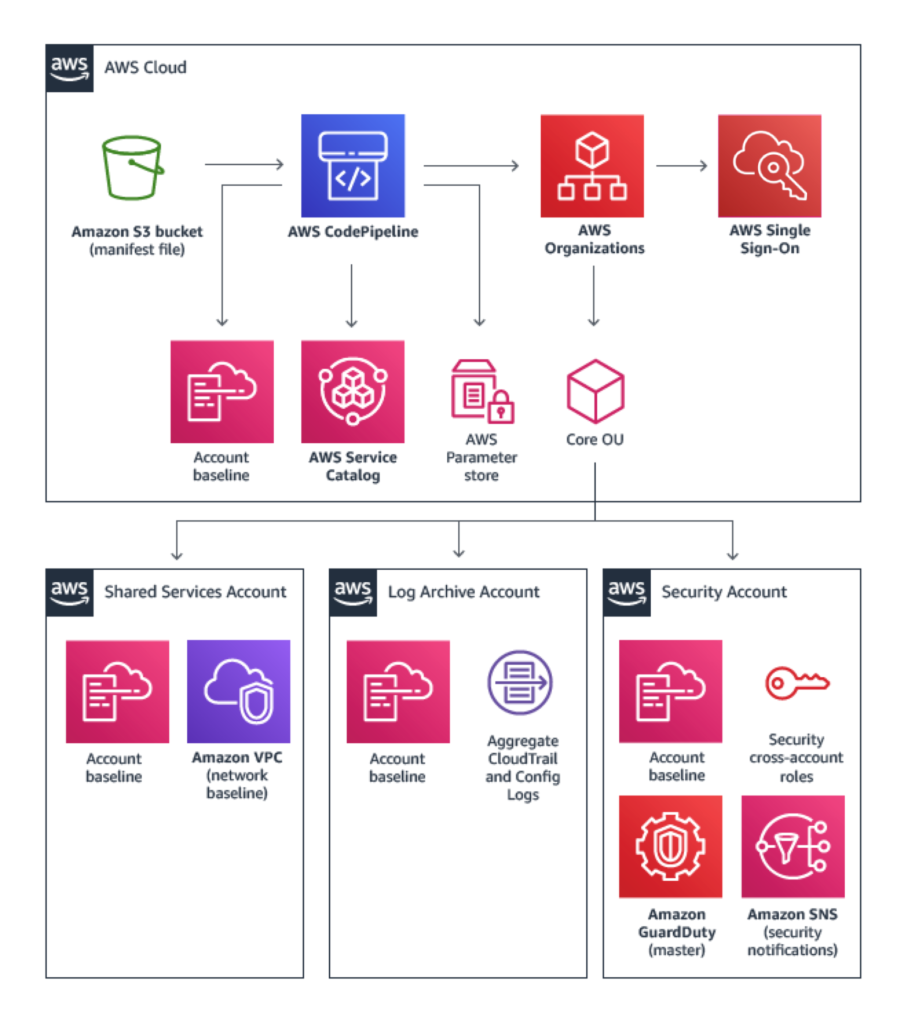
The Landing Zone (LZ) concept gives users a safe and comfortable place to “land” in the Cloud. In the past few years, we’ve seen continued improvements and innovation from AWS in this area, going from a Landing Zone as a AWS Solution, to launching AWS Organizations, AWS SSO and AWS Control Tower services to help customers manage multi-AWS-account organizations.
However, due to the GCC’s nature of being cloud agnostic, it seems unlikely that GCC 2.0 will tap on the above-mentioned AWS services for managing multiple tenant accounts. LZ will be realized with Terraform, with its code being inner-sourced (“open source” to GCC users). I am looking forward to see how this will be implemented.
Closing Thoughts
GCC 2.0 is set to be GA on 1st April 2022 with AWS first, amidst the early adoption program already in progress.
There are many exciting features to look forward to with GCC 2.0, but the jury is still out on fulfilling its vision of being “light touch”, more secure and easier to use. I will try to cover more publicly available information once I have them.
On a side note, I am pleasantly surprised that many of the same GovTechies from STACK-X sessions back in 2019 are still working on GCC 2.0. This gives me a higher level of confidence on the longevity and continuity of the GCC platform. Community outreach and open communication channels to obtain feedback seem to be effective as well in shaping GCC 2.0.
Thanks for reading to the end. I hope you enjoyed reading this as much as I enjoyed writing it. Reach out to me on LinkedIn if you’d like to discuss GCC 2.0 with me.
